According to a new report from Der Spiegel based on internal NSA documents, the signals intelligence agency’s elite hacking unit (TAO) is able to conduct sophisticated wiretaps in ways that make Hollywood fantasy look more like reality. The report indicates that the NSA, in collaboration with the CIA and FBI, routinely and secretly intercepts shipping deliveries for laptops or other computer accessories in order to implant bugs before they reach their destinations. According to Der Spiegel, the NSA’s TAO group is able to divert shipping deliveries to its own “secret workshops” in a method called interdiction, where agents load malware onto the electronics or install malicious hardware that can give US intelligence agencies remote access.
While the report does not indicate the scope of the program, or who the NSA is targeting with such wiretaps, it’s a unique look at the agency’s collaborative efforts with the broader intelligence community to gain hard access to communications equipment. One of the products the NSA appears to use to compromise target electronics is codenamed COTTONMOUTH, and has been available since 2009; it’s a USB “hardware implant” that secretly provides the NSA with remote access to the compromised machine.
 This tool, among others, is available to NSA agents through what Der Spiegel describes as a mail-order spy catalog. The report indicates that the catalog offers backdoors into the hardware and software of the most prominent technology makers, including Cisco, Juniper Networks, Dell, Seagate, Western Digital, Maxtor, Samsung, and Huawei. Many of the targets are American companies. The report indicates that the NSA can even exploit error reports from Microsoft’s Windows operating system; by intercepting the error reports and determining what’s wrong with a target’s computer, the NSA can then attack it with Trojans or other malware.
This tool, among others, is available to NSA agents through what Der Spiegel describes as a mail-order spy catalog. The report indicates that the catalog offers backdoors into the hardware and software of the most prominent technology makers, including Cisco, Juniper Networks, Dell, Seagate, Western Digital, Maxtor, Samsung, and Huawei. Many of the targets are American companies. The report indicates that the NSA can even exploit error reports from Microsoft’s Windows operating system; by intercepting the error reports and determining what’s wrong with a target’s computer, the NSA can then attack it with Trojans or other malware.
Sometimes the NSA hops on an FBI jet for high-tech raids
The Der Spiegel report, which gives a broad look at TAO operations, also highlights the NSA’s cooperation with other intelligence agencies to conduct Hollywood-style raids. Unlike most of the NSA’s operations which allow for remote access to targets, Der Spiegel notes that the TAO’s programs often require physical access to targets. To gain physical access, the NSA reportedly works with the CIA and FBI on sensitive missions that sometimes include flying NSA agents on FBI jets to plant wiretaps. “This gets them to their destination at the right time and can help them to disappear again undetected after even as little as a half hour’s work,” the report notes.
The NSA currently faces pressure from the public, Congress, federal courts, and privacy advocates over its expansive spying programs. Those programs, which include bulk telephone surveillance of American citizens, are said by critics to violate constitutional protections against unreasonable searches, and were uncovered earlier this year by whistleblower Edward Snowden. Beyond the programs that scoop up data on American citizens, Snowden’s documents have also given a much closer look at how the spy agency conducts other surveillance operations, including tapping the phones of high-level foreign leaders.
RELATED ARTICLE:
THE EDGE OF THE ABYSS: NSA’S ALL-SEING MACHINE
“I know the capability that is there to make tyranny total in America, and we must see to it that this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss. That is the abyss from which there is no return.”
Senator Frank Church on Meet The Press, 1975
On November 4th, 1952, a new federal agency was created in secret, chartered with spying on foreign adversaries around the world. There was no mention in the press. There was no discussion on the floor of Congress. The existence of the agency appeared nowhere in the Federal Register.
Since then, much of what the public knows about the National Security Agency has been the stuff of Sneakers and West Wing legend. Its budget — part of the secretive US “black budget” — is largely unknown. The NSA has even been nicknamed “No Such Agency” because of its extreme secrecy. Its headquarters, located in Fort Meade, Maryland, literally resembles a giant black box.
But this year, the box was cracked open.

An unprecedented cache of the NSA’s secrets were stolen in bulk this year by a single independent contractor with administrative access to the intelligence community’s network — a feat unmatched by previous NSA whistleblowers who provided the world mostly with eyewitness accounts of the agency’s behavior. The former contractor, Edward Snowden, fled the United States before teaming up with journalists to disseminate the NSA files, and now resides in Russia where he sought asylum and protection from US prosecution.
We now know that nearly five decades after its creation, the NSA began to operate what would become a global surveillance network of breathtaking scale. Today, it collects records about every phone call placed in the United States. It works with overseas partners and telecommunications companies to directly tap into the arteries of the internet, and scoops up massive amounts of data including emails, chats, VoIP calls, and more. It collects billions of records every year, many belonging to ordinary US citizens with no suspicion of wrongdoing.
Nearly each week since June 5th when The Guardian published the first Snowden documents, new internal files and facts about bulk NSA surveillance have been released. Snowden is said to have leaked upward of 50,000 files from the government. The journalists to whom he’s passing the data, like Glenn Greenwald, say more revelations are coming.
Signals

Signals intelligence, or SIGINT, encompasses the interception of electronic signals and communications intelligence, and was an enormous factor in 20th-century wars and diplomacy. In World War I, when radio was still a novel concept, the US and other nations primarily gained access to communications by tapping undersea telephone cables. The United States entered World War I after British intelligence intercepted a coded telegram in which the German Empire proposed that Mexico join Europe’s Central Powers, if the US joined the fight on the side of Britain and France.
The role of SIGINT was dramatically expanded in World War II, which was a truly global war with widespread use of radio and encoded communications. Cryptography and cryptanalysis were essential to all sides, and intensive code-breaking efforts aided Allied forces greatly in their victory.

In 1952, President Harry Truman issued a memo which led to the creation of the National Security Agency, consolidating the military’s SIGINT responsibilities. In the decades following, the NSA would play a crucial role in signals intelligence during the Cold War, the Vietnam War, and in the modern war on terrorism.
Even before the pivotal national security era that began on September 11th, 2001, the NSA recognized the SIGINT opportunities presented by the internet. In an unclassified December, 2000 transition report, the agency outlined the intelligence landscape, noting “the explosion in global communications,” and a need to be at the forefront of advances in technology. The document states that “to perform both its offensive and defensive missions, NSA must ‘live on the network.’” As leaked documents from Edward Snowden show, the NSA has largely accomplished the mission it envisioned more than a decade ago. But according to critics, it has systematically dodged or violated federal law in doing so.

Following 9/11, the NSA’s ability to gather the communications of US citizens was greatly enhanced by the Patriot Act of 2001, the Protect America Act of 2007, the FISA Amendments Act of 2008, and secret interpretations of US law that have only recently begun to enter the public view — interpretations that have surprised and concerned even the Patriot Act’s original authors. Documents leaked this year have revealed that the NSA is operating a massive global surveillance network, one that once seemed only possible in Hollywood fantasy, and that privacy advocates and some politicians fear is highly intrusive, dangerous, and unwarranted. Furthermore, the surveillance of US citizens appears to go well beyond the NSA’s explicit charge of collecting data “for foreign intelligence and counterintelligence purposes” as set forth in Executive Order 12333. Instead of just collecting data on foreigners, the NSA now appears to want all available communications data in the pursuit of terrorists.
Intelligence
If you have a phone and a computer, it’s likely that practically everything you do generates a signal: your bank records, your emails, your phone calls, your text messages, and your sexy Snapchats. At some point, they’re likely to be handled by companies like Google, Facebook, Apple, or AT&T. And like the NSA, your records live on the network.
Unlike documents in a safe or money in a bank vault, your electronic files probably aren’t sitting in one place, especially if they’re handled by global service providers like Google or Yahoo. In the age of global cloud data, it’s possible (even likely) that information you store with a US company is exchanged between servers located outside of US borders.
Because of legal restrictions regarding how the NSA is able to collect and search data, there’s an important distinction between the types of intelligence that the agency scoops up. There’s “content,” which is, naturally, the substantive matter of your communications. That includes the stuff inside your emails, the things you say in your phone calls, and the family photo album you store in Dropbox.
Then there’s “metadata,” which is “data about data:” it’s information about your content. For phone records that includes data like the times, addresses, and durations of phone calls. For email addresses that includes stuff like the IP addresses and the email addresses of the sender and recipient, and the date and time of the email.
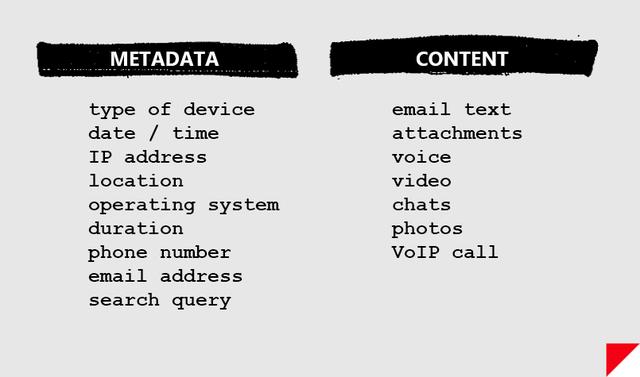
A metadata map can tell someone much more about your life than a single email
The intelligence community and some government officials argue that metadata isn’t really content. But metadata can say a lot about a person, including who, when, and even where they talked to someone. That kind of information is particularly sensitive for people like journalists who have confidential informants, but it’s also potentially quite damaging for the average person who may, for instance, have called an addiction hotline or sent a political donation over the phone.
So how does the NSA collect this information? Broadly speaking, there are two approaches: “downstream” collection, which involves explicit, yet secret requests to technology companies for user data, and “upstream” collection, which is like a phone wiretap, pulling data directly from telecommunication cables. The US government doesn’t let companies give specifics about the amount of data they are forced to give up each year, and upstream collection methods have remained closely guarded secrets. Still, thanks to this year’s leaks, we know more than ever about how the NSA gets its hands on electronic data.
DOWNSTREAM
One of the NSA’s largest downstream efforts is the “Associational Tracking Program,” a telephone surveillance dragnet which collects phone call metadata from companies including AT&T, MCI, Sprint, and Verizon. A 2006 report from USA Today suggested that the NSA’s goal was to “create a database of every call ever made” within the United States. In June, The Guardian published a secret court order which requires Verizon on an “ongoing, daily basis” to hand the NSA information on all telephone calls made within the US and between the US and other countries: including the numbers of both parties on a call, location data, call duration, unique identifiers, and the time and duration of calls. Obviously, with such a comprehensive and indiscriminate dragnet, millions of phone records are routinely collected on citizens who are not suspected of any wrongdoing.
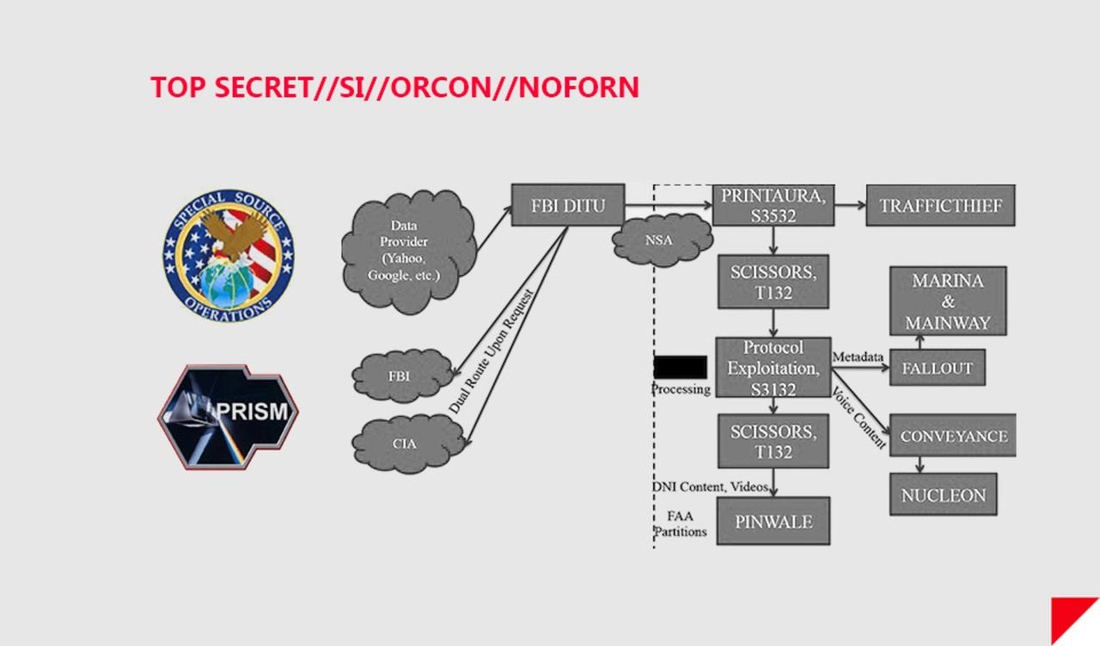
The other notable downstream effort, also revealed by The Guardian with help from Edward Snowden, is PRISM: a surveillance program that allows the government to store and search for content belonging to people who use services from Google, Facebook, Apple, Microsoft, AOL, Yahoo, and other companies. PRISM is an extension of President Bush’s “Terrorist Surveillance Program,” which began with, as the AP reported on June 15th, in-person data requests from the FBI in the years following 9/11. The requests were so extensive that, according to the AP, some inside Microsoft called it “Hoovering” after FBI director J. Edgar Hoover, who notoriously dug up dirt on Americans with impropriety.

But while data requests began with the FBI, the Protect America Act of 2007 marked a shift in the government’s strategy, authorizing the NSA, an agency dedicated to foreign surveillance, to begin collecting this user data in collaboration with tech companies. The companies, by government mandate, set up streamlined systems for data transfers. Like the bulk telephone surveillance program, no warrants or specific targets are required for data collection; in PRISM’s case, the secret Foreign Intelligence Surveillance Court authorizes a yearly, classified request from the attorney general and the director of national intelligence which gives general guidelines on how the government intends to collect intelligence on foreigners.
Shortly after details about the bulk telephone surveillance program and PRISM were revealed, President Obama confirmed their existence, and defended them as limited, legal programs which help to prevent terror attacks. Since the president’s admission, intelligence community officials and supporters in Congress have mounted similar defenses of the programs.
UPSTREAM
When PRISM was originally reported, The Washington Post and The Guardian suggested something about the program more sinister than reality: that the NSA had “direct access” to the servers of major email and electronic communication providers. While Google, Facebook, and other companies implicated in PRISM collaboration flatly denied any arrangement that would hand the NSA unfettered access to data, the back-and-forth over direct access was window dressing to the NSA’s much larger effort: upstream collection, which sucks data directly from the internet as it passes through the cables that make up the network.
The NSA has developed partnerships with telecommunications companies and foreign intelligence-gathering agencies to gain access to international fiber-optic cables, switches, and routers, allowing it to pull enormous volumes of information from the internet. The most egregious example of the partnership between a telecom giant and the US government came seven years ago, when former technician Mark Klein revealed that the NSA had installed network routing equipment inside a secret room called “641A” at an AT&T switching hub in San Francisco. It’s still unclear how many access points the NSA has developed.
The NSA’s data doesn’t just come from its own wiretaps. As The Guardian notes, most of the world’s communications pass through the US or the UK, giving the NSA a “home-field advantage” when it comes to intercepting traffic. On June 21st, The Guardian reported that the NSA’s British counterpart, the Government Communications Headquarters (GCHQ), also taps fiber-optic lines to intercept and store massive amounts of data on the web. Through a program called Tempora, the data is shared between the UK and the NSA, which have maintained an intimate relationship since World War II.
Of course, some of the data that passes over those cables is encrypted, and while it’s still not likely that the NSA is able to crack the most powerful standards with brute force, the agency has explored other methods for making encryption a moot point. Over the years, the NSA has worked to insert backdoors in cryptographic standards; the agency has purposefully spread at least one bad algorithm, and NSA algorithms are the basis for many products, including some that protect sensitive government data. The National Institute for Standards and Technology, a federal group that sets national standards for data protection, is now reviewing all of its previous cryptographic recommendations as a result of allegations of NSA meddling. Cryptographers still don’t know how widespread the issue is.
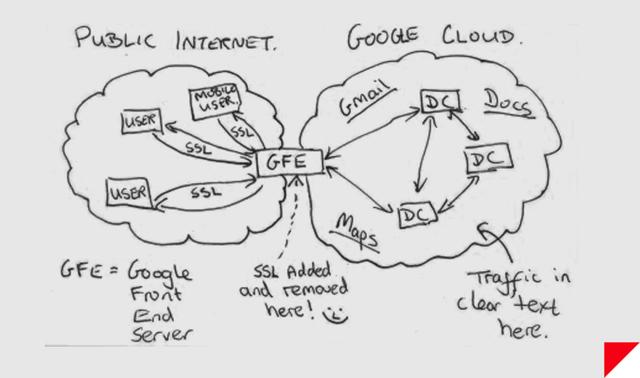
“It’s really outrageous that the NSA was looking between the Google data centers.”
Even more troubling than public internet wiretaps, a November 4th report from The Washington Post revealed that the NSA, through a project called MUSCULAR, allegedly exploits data links in Google and Yahoo’s global networks to tap user data before it’s encrypted. Such data collection is roughly the kind that so worried privacy advocates when PRISM was initially reported, except that this kind of “direct access” to Google and Yahoo’s data is unauthorized by the tech companies. In response to the report, Google executive Eric Schmidt told The Wall Street Journal that “it’s really outrageous that the National Security Agency was looking between the Google data centers, if that’s true.”
BEYOND COUNTERTERRORISM
Aside from its recent foray into mass data collection for counterterrorism purposes, part of the NSA’s core mission is foreign intelligence. While this activity presents different concerns from the legal issues surrounding collection of data on US citizens, revelations about NSA spying on foreign nations, political leaders, diplomats, militaries, and other organizations has nonetheless caused the US government a great deal of consternation in recent months.
Given the NSA’s original mandate, it’s no real surprise that the agency spies on foreign governments, but several Snowden leaks regarding foreign spying have shed light on the extent of the NSA’s capabilities. The governments of France, Brazil, Germany, and others have harshly criticized US spying efforts, causing an immeasurable amount of diplomatic blowback. But they, too, likely conduct analogous intelligence-gathering efforts; on November 5th, Brazil admitted to spying on US diplomats after it blasted NSA surveillance of the same kind.
While governments spying on each other may not be a surprise to anyone, the leaks show how the NSA has been able to conduct serious intelligence-gathering operations without significant oversight. On October 24th, The Guardian reported that the NSA spied on the phone calls of 35 foreign leaders, including Germany’s Angela Merkel, without the knowledge or approval of President Obama. Obama allegedly spent five years in office without knowing that the NSA was spying on world leaders because, by the NSA’s own account, the agency was conducting too many operations for the president to keep track of.
Protocols
FORCE OF LAW

The government uses several legal pegs to justify its mass surveillance program. Some are based on outdated laws, like the 1986 Electronic Communications Privacy Act (ECPA), while others are based on technical definitions of things like “surveillance” and metadata, which have separate conventional and legal understandings. Even the meaning of “data collection” is up for grabs; in a June 9th interview with NBC’s Andrea Mitchell, the director of national intelligence, James Clapper, deflected criticism for bulk surveillance, saying that “collection of US persons’ data would mean taking [a] book off the shelf and opening it up and reading it.” (The intelligence community argues that unless it actually looks at the data it collects, it hasn’t actually collected any data).
The rules governing what kind of data the government can collect on you from the internet aren’t the same as those which keep it from rifling through your filing cabinet. The ECPA, a law established before things like Gmail existed, allow the government to seize massive amounts of data without warrants, with impunity. Under the ECPA, law enforcement can search your email without a warrant as long as they’ve been stored on cloud servers for at least 180 days and have been declared “relevant” to an investigation, which is a fairly low bar for the government to meet.
Outdated laws provide little protection for your content, and even less for your metadata

Protection for metadata is even worse. An important 1976 court decision in Smith v. Maryland established the government’s key defense of metadata collection. Using the “third party” doctrine, the court decided that the data generated by using telecommunications, like phone call records, count as data “given” to a third party. This means that you have no “reasonable expectation” of privacy for telecommunications metadata. One federal judge even suggested recently that the only way you should expect privacy is to keep your phone turned off.
The ECPA and Smith v. Maryland don’t authorize the kind of mass spying we now see today, but compliment other laws that have been interpreted in secret to allow mass surveillance. The NSA’s surveillance programs rely on two key statutes, section 702 of the FISA Amendments Act (FAA) and Section 215 of the Patriot Act. The FAA allows the collection of communications content under programs like PRISM, while the Patriot Act authorizes the collection of metadata from phone companies.
Secret interpretations of the statutes by the Foreign Intelligence Surveillance Court have granted the intelligence community much broader authority than they were originally intended to allow. In one of the first hearings this year on bulk telephone surveillance, following initial leaks, members of the House Judiciary Committee expressed outrage over the program. “I feel very uncomfortable about using aggregated metadata on hundreds of millions of Americans — everybody, including every member of Congress, and every citizen who has a phone in the US,” Rep. John Conyers (D-MI) said. “This is unsustainable, it’s outrageous, and must be stopped immediately.”
TARGETING AND MINIMIZATION
The government argues that the bulk collection of sensitive data is managed responsibly through a “targeting and minimization” process intended to prevent or correct the inappropriate interception, analysis, or dissemination of data belonging to innocent US citizens. But, as declassified court opinions have revealed, the NSA’s violations of the law are legion; the agency violated the rules thousands of times in 2011 and 2012 alone.
To access collected data, NSA analysts have to input search terms called “selectors” into a system like PRISM, which then “tasks” data from other collection sites. Analysts are not permitted to specifically target someone who’s “reasonably believed” to be a US person communicating within the United States, but according to The Washington Post an analyst only needs to have at least “51 percent” certainty that their target is foreign — just a little better than a coin flip. Even then, the NSA’s use of “contact chaining,” which allows analysts to collect records up to “three hops” from a target, means that the NSA can collect records on not only a target’s contacts, but their contacts’ contacts as well. According to The Guardian, that means someone with roughly 400 friends on Facebook could potentially be linked to over 10 million contacts.
Someone with 400 friends on Facebook could potentially be linked to over 10 million contacts
While the NSA admits to some level of “incidental” collection of data belonging to US citizens and downplays it as insignificant, there have been flagrant ethical and legal violations of data collection and use. In addition to the thousands of “compliance breaches” that resulted in the tracking of suspects in violation of FISA court rulings, The Wall Street Journal reported in August that several NSA officers had used the surveillance apparatus to spy on love interests.
Other misuses are more troubling. An August 5th report from Reuters alleged that a secretive Drug Enforcement Administration unit has been using NSA data to launch criminal investigations of US citizens for drug crimes, and that the DEA covered up its relationship with the NSA by training federal agents to retroactively recreate the investigative trail.

Echoes
There is currently no clear path to reform. All three branches of US government have, in some measure, enabled, allowed, or justified the existence and continued use of unprecedented NSA programs that collect data on American citizens.
President Obama, who is the NSA’s top brass as commander-in-chief of the US military, has shown no genuine interest in reforming the agency. In addition to broadly defending the bulk surveillance programs before the public, his NSA review panel — created in response to leaks from Edward Snowden — is filled with insiders who are unlikely to provoke change.
Congress, which is responsible for oversight of the intelligence community, is currently divided on the issue of mass surveillance. It has arguably failed to fully meet its oversight role, neglecting to collect adequate information from the NSA about its activities, and opting not to hold intelligence officials accountable for blatantly lying to Congress and the public. For instance Director of National Intelligence James Clapper and NSA Director Keith Alexander each, in separate Congressional hearings, testified that the NSA was not collecting data on US persons. In fact, is has been collecting data on billions of phone records and other information belonging to US citizens.
Ironically, the Select Committee on Intelligence, the Congressional body charged with overseeing the NSA and other intelligence groups, was established precisely to prevent domestic surveillance abuses. The Church Committee, established in 1975 to audit the intelligence community following Watergate, learned that in the 1950s the CIA and the FBI had intercepted and collected the contents of over more than 215,000 pieces of mail belonging to US citizens. And indeed, surveilling US citizens is in the NSA’s pedigree; recently, declassified documents revealed that Martin Luther King Jr, Muhammad Ali, and other prominent Americans were targets of NSA surveillance during the Vietnam War, from 1967 to 1973.
The current chair of the Senate Select Committee on Intelligence, Senator Dianne Feinstein (D-CA), is one of the most ardent supporters of NSA bulk surveillance and originally downplayed the Verizon leak as business-as-usual. In October, Feinstein took out an op-ed in USA Today, arguing that metadata deserves no Fourth Amendment protection. On October 31st, Feinstein passed an NSA “improvement” bill in Congress offering no real reform; in fact, the Feinstein bill legitimizes the mass data collection that has so far been justified in secret.
“What happens to our civil liberties if the surveillance state is allowed to grow unchecked?”
Some lawmakers, however, are working to reverse mass surveillance of US citizens. On October 29th, Senator Patrick Leahy (D-VT) and Patriot Act co-author Rep. Jim Sensenbrenner (R, WI) introduced the “Freedom Act,” which would end bulk data collection by rewriting Section 215 of the Patriot Act and creating new limits on FAA Section 702. Others, like Senator Ron Wyden, (D, OR), have issued repeated warnings about the NSA’s capabilities. “The combination of increasingly advanced technology with a breakdown in the checks and balances that limit government action could lead to a surveillance state that cannot be reversed,” Wyden said earlier this year. “What happens to our government, our civil liberties, and our basic democracy if the surveillance state is allowed to grow unchecked?”
Finally, the judicial branch, which has secretly authorized mass NSA spying over the past decade in collaboration with the executive and legislative branches, could play a role in reform. While some tech companies are currently suing the government to release gag orders preventing them from informing customers about how many data requests the government makes, such efforts are largely cosmetic, and won’t impact data collection. The American Civil Liberties Union, Public Knowledge, the Open Technology Institute, Free Press, Human Rights Watch, and others have sued to end the telephone dragnet, arguing that the collection violates the First, Fourth, and Fifth Amendments.
There’s still a mountain of information we don’t have about the National Security Agency — including information about the NSA’s methods that may never come to light. Of course, that’s to be expected; many of the NSA’s activities must be conducted in secret to have any kind of efficacy. But today’s NSA is exceptional in that its technological ability appears to have vastly exceeded both its original mandate and the ability of the government to conduct effective oversight. President Obama has at least conceded this point. “In some ways, the [NSA’s] technology and budget and capacity have outstripped the constraints,” Obama said in a November 7th interview. “We’ve got to rebuild those.”
